Adding a server to the STENG - NEW! 🚀
To add a server to a STENG you must follow these steps:
- In the STENG, Clusters and Servers page, click on the NEW SERVER button.
- In the dialog window, select the protocol of the server you are adding among those available.
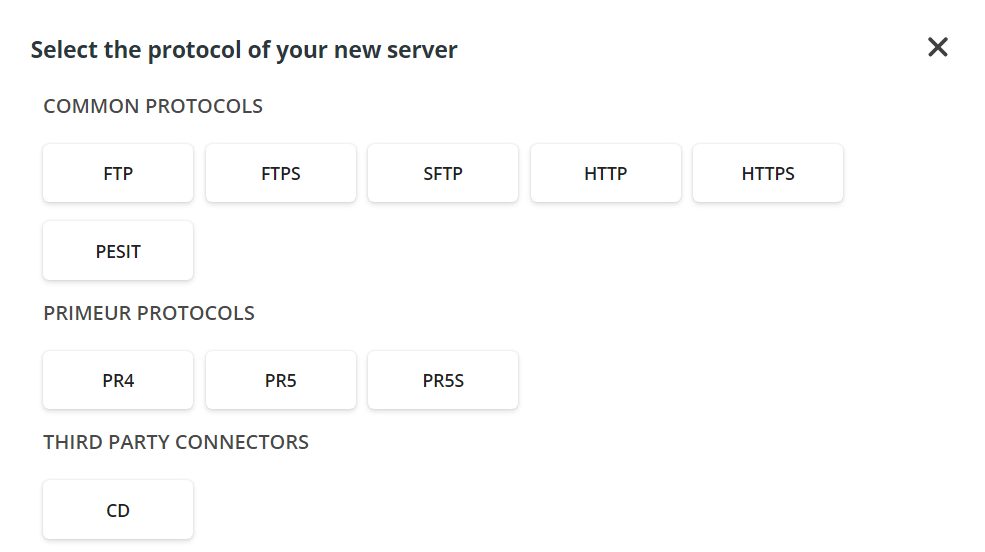
- Depending on the selected protocol, different dialog windows will appear. You can find a detailed description of the fields available for each protocol in the Protocol and fields section below. Fields with the asterisk * are mandatory.
These fields are common to all protocols:
- Server Name and Description.
- Cluster associated to the server.
- Default Status of the server: enabled or disabled. - When done, click the Continue button to have a recap of the parameters entered. Click the Save button to deploy the server on the STENG.
- All STENGs must have the same number of servers to ensure high reliability. Therefore, when adding a server to a STENG, the last screen with list all STENGs and when saving, the server will be added to all missing STENGs. Likewise, when deleting a server, it will be deleted from all STENGs to keep the same number of servers in all STENGs.
Protocols and fields
These fields are common to all protocols:
- Server Name and Description.
- Cluster associated to the server.
- Default Status of the server: enabled or disabled.
Fields with the asterisk * are mandatory.
FTP
| Connection | |
|---|---|
| PORT * | Enter the port to connect to the server. This is the TCP/IP port the server will listen to in the STENG node. |
| PORT RANGE | Enter the range for the ports the server will listen to. |
| ACTIVE DATA CONNECTION LOCAL ADDRESS | Enter the local address for active data connection |
| PASSIVE EXTERNAL ADDRESS | This field must be filled in only if OPERATING MODE is set to PASSIVE and will contain the address used for passive connections. If the server is behind NAT, insert the external IP address. |
| MAX SESSION | Specify the maximum number of active sessions. |
| CONNECTION TIMEOUT | Define the number of seconds to wait without network activity before closing a session due to inactivity. Default value: 60. |
| ACTIVE DATA CONN LOCAL OUTPORT | If the OPERATING MODE is set to ACTIVE, enter the port the client must connect to. |
| OPERATING MODE | How data connection is established, possible values: - ACTIVE (default value) - PASSIVE When setting the “Active mode file transfer”, the client will establish a control connection to the server, and the server will establish a data connection back to the client. With “Passive mode file transfer”, the client will establish both a control connection and a data connection to the server. |
| DMZ mode | |
|---|---|
| NONE (default) | No session proxying through DMZ Gateway is applied. |
| PORT_FORWARDING | Incoming/Outgoing connections to/from the STENG server will be proxied inside an SSL tunnel without being validated in advance. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. |
| SESSION_TERMINATION | The server session will be terminated inside the DMZ Gateway before data is sent to the STENG server. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER PORT *: DMZ server port used for connection. DMZ PASSIVE EXTERNAL ADDRESS: When an FTP client wants to transfer data using Passive Mode, the PASV command is issued. Upon receiving that command, the FTP server responds with the server’s IP address and the port number the client must connect to. DMZ PORT RANGE: Range of ports for passive data connection. |
🚀 To change any DMZ port of an FTP server that belongs to a peer, select the server you want to update. Next, click the pencil icon in the top-right corner of the server card. Enter the new port or ports in the appropriate fields. Finally, click the SAVE button to confirm your changes. Remember that the new port number will only affect the peer's selected server.
FTPS
| Connection | |
|---|---|
| PORT * | Enter the port to connect to the server. This is the TCP/IP port the server will listen to in the STENG node. |
| PORT RANGE | Enter the range for the ports the server will listen to. |
| SERVER KEYLABEL * | Enter the Key identifier of the keystore store to select the Private Key and Certificate to create an SSL connection. |
| ACTIVE DATA CONNECTION LOCAL ADDRESS | Enter the local address for the active data connection. |
| PASSIVE EXTERNAL ADDRESS | This field must be filled in only if OPERATING MODE is set to PASSIVE and will contain the address used for passive connections. If the server is behind NAT, insert the external IP address. |
| MAX SESSION | Specify the maximum number of active sessions. |
| CONNECTION TIMEOUT | Define the number of seconds to wait without network activity before closing a session due to inactivity. Default value: 60. |
| ACTIVE DATA CONN LOCAL OUTPORT | If the OPERATING MODE is set to ACTIVE, enter the port the client must connect to. |
| REQUIRE CLIENT AUTHENTICATION | Enable the toggle button if you want the server to require SSL Client Authentication from the client that is connecting. If enabled, the CLIENT CERTIFICATION MATCH field appears, and the appropriate option must be selected in the drop-down menu – detailsare in the field below. |
| CLIENT CERTIFICATION MATCH | This field appears if the REQUIRE CLIENT AUTHENTICATION button is enabled. It defines if the Certificate required for Client Authentication will be matched and how. Possible values: - NONE: the Certificate will not be matched. The presence of a valid Certificate is enough to proceed. This is the less secure option. - CNEQUALS (default value): the Common Name field of the Certificate must be the same as the user name. This is the most restrictive option. - CNCONTAINS: the Common Name field of the Certificate must contain the user name. |
| OPERATING MODE | How data connection is established, possible values: - ACTIVE (default value) - PASSIVE When setting the “Active mode file transfer”, the client will establish a control connection to the server, and the server will establish a data connection back to the client. With “Passive mode file transfer”, the client will establish both a control connection and a data connection to the server. |
| DATA PROTECTION | Data channel protection. Possible values: - PROTECTED: Force data channel protection - CLEARTEXT: No data channel protection |
| SSL CONTROL | Possible values: - EXPLICIT (recommended) - IMPLICIT Selecting EXPLICIT, an explicit SSL/TLS connection will be set via AUTH command. Selecting IMPLICIT, an implicit SSL/TLS connection will be set. Most FTP/S Servers listen for implicit connections to port 990. |
| AUTHENTICATION PROTOCOL | Select the SSL authentication protocol. Possible values: - ALL - ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1_1 TLSv1_2 TLSv1_3 SSLv2Hello |
| ACCEPTED CIPHER SUITES | Select the cipherSuites accepted to establish SSL connection. For a list of all accepted Cipher Suites, follow this link. |
| DMZ mode | |
|---|---|
| NONE (default) | No session proxying through DMZ Gateway is applied. |
| PORT_FORWARDING | Incoming/Outgoing connections to/from STENG server will be proxied inside an SSL tunnel without being validated in advance. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. |
| SESSION_TERMINATION | The server session will be terminated inside the DMZ Gateway before data is sent to Sthe TENG server. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER PORT *: DMZ server port used for connection. SERVER KEYLABEL: Select the label of the private key to be used by the FTPS server exposed in the DMZ Gateway. REQUIRE CLIENT AUTHENTICATION: Enable the toggle button if you want the server to require SSL Client Authentication to the client that is connecting in DMZ. If enabled, the DMZ CLIENT CERTIFICATION MATCH field appears, and the appropriate option must be selected in the drop-down menu – details are in the field below. If the FTPS client on DMZGateway is connecting to an FTPS Server with clientAuthentication=true on the STENG, check the client certificate coming from the client FTPS into the Untrusted Cache. Then, trust the client certificate and check the Trust Store. DMZ CLIENT CERTIFICATION MATCH: This field appears if the Require Client Authentication button is enabled. It defines if the Certificate required for Client Authentication will be matched and how. Possible values: - NONE: the Certificate will not be matched. The presence of a valid Certificate is enough to proceed. This is the less secure option. - CNEQUALS (default value): the Common Name field of the Certificate must be the same as the user name. This is the most restrictive option. - CNCONTAINS: the Common Name field of the Certificate must contain the user name. ACCEPTED CIPHER SUITES: It lists SSL/TLS cipher suites available in the FTP/S server and exposed in the DMZ Gateway. Select the cipherSuites accepted. For a list of all accepted Cipher Suites, follow this link. DATA PROTECTION: Set whether the data channel must be protected via SSL in the FTP/S server exposed in DMZ Gateway. Possible values: - PROTECTED: Force data channel protection - CLEARTEXT: No data channel protection SECURITY PROTOCOL: Possible values: - ALL - ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1.1 TLSv1.2 SSLv2Hello SSL PROTOCOL: Select a secure server profile activation mechanism in FTP/S server exposed in DMZ Gateway (see Connection/SSL Control). DMZ PASSIVE EXTERNAL ADDRESS: When an FTP/S client wants to transfer data using Passive Mode, the PASV command is issued. Upon receiving that command, the FTP/S server responds with the server’s IP address and the port number the client must connect to. DMZ PORT RANGE: Range of ports for passive data connection |
🚀 To change any DMZ port of an FTPS server that belongs to a peer, select the server you want to update. Next, click the pencil icon in the top-right corner of the server card. Enter the new port or ports in the appropriate fields. Finally, click the SAVE button to confirm your changes. Remember that the new port number will only affect the peer's selected server.
SFTP
| Connection | |
|---|---|
| PORT * | Enter the port to connect to the server. This is the TCP/IP port the server will listen to in the STENG node. |
| SERVER KEYLABEL * | Enter the Key identifier of the keystore store to select the Private Key and Certificate to create an SSL connection. |
| MAX SESSION | Specify the maximum number of active sessions. |
| CONNECTION TIMEOUT | Define the number of seconds to wait without network activity before closing a session due to inactivity. Default value: 60. |
| ALLOW SCP | Switch to disable or enable the SCP protocol. Possible values: YES and NO. |
| ALLOWED CLIENT AUTHENTICATION MODES * | This field refers to the SSH client authentication mechanism. Possible values: PUBLICKEY PASSWORD PASSWORD_AND_PUBLICKEY PASSWORD_OR_PUBLICKEY |
| ACCEPTED CIPHER SUITES | Select the cipherSuites accepted to establish an SSL connection. For a list of all accepted Cipher Suites, follow this link. |
| MAC ALGORITHMS | Possible values: HMAC_MD5 HMAC_SHA1 HMAC_MD5_96 HMAC_SHA1_96 HMAC_SHA256 HMAC_SHA2_256 HMAC_SHA2_512 |
| KEY EXCHANGE ALGORITHMS | Possible values: DIFFIE_HELLMAN_GROUP1_SHA1 DIFFIE_HELLMAN_GROUP14_SHA1 DIFFIE_HELLMAN_GROUP14_SHA256 DIFFIE_HELLMAN_GROUP15_SHA512 DIFFIE_HELLMAN_GROUP16_SHA512 DIFFIE_HELLMAN_GROUP17_SHA512 DIFFIE_HELLMAN_GROUP18_SHA512 DIFFIE_HELLMAN_GROUP_EXCHANGE_SHA1 DIFFIE_HELLMAN_GROUP_EXCHANGE_SHA256 ECDH_SHA2_NISTP256 ECDH_SHA2_NISTP384 ECDH_SHA2_NISTP521 |
| DMZ mode | |
|---|---|
| NONE (default) | No session proxying through DMZ Gateway is applied. |
| PORT_FORWARDING | Incoming/Outgoing connections to/from the STENG server will be proxied inside an SSL tunnel without being validated in advance. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER KEYLABEL: Select the label of the private key to be used by the SFTP server exposed in the DMZ Gateway. CLIENT AUTHENTICATION MODES: This field refers to the SSH client authentication mechanism. Possible values: PUBLICKEY PASSWORD PASSWORD_AND_PUBLICKEY PASSWORD_OR_PUBLICKEY MAC ALGORITHMS: Possible values: HMAC_MD5 HMAC_SHA1 HMAC_MD5_96 HMAC_SHA1_96 HMAC_SHA256 HMAC_SHA2_256 HMAC_SHA2_512 KEY EXCHANGE ALGORITHMS: Possible values: DIFFIE_HELLMAN_GROUP1_SHA1 DIFFIE_HELLMAN_GROUP14_SHA1 DIFFIE_HELLMAN_GROUP14_SHA256 DIFFIE_HELLMAN_GROUP15_SHA512 DIFFIE_HELLMAN_GROUP16_SHA512 DIFFIE_HELLMAN_GROUP17_SHA512 DIFFIE_HELLMAN_GROUP18_SHA512 DIFFIE_HELLMAN_GROUP_EXCHANGE_SHA1 DIFFIE_HELLMAN_GROUP_EXCHANGE_SHA256 ECDH_SHA2_NISTP256 ECDH_SHA2_NISTP384 ECDH_SHA2_NISTP521 ACCEPTED CIPHER SUITES: It lists SSL/TLS cipher suites available in the SFTP server and exposed in the DMZ Gateway. Select the cipherSuites accepted. For a list of all accepted Cipher Suites, follow this link. |
| SESSION_TERMINATION | The server session will be terminated inside the DMZ Gateway before data is sent to the STENG server. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER PORT *: Enter the DMZ server port to be used for the connection. SERVER KEYLABEL: Select the label of the private key to be used by the SFTP server exposed in the DMZ Gateway. CLIENT AUTHENTICATION MODES: This field refers to the SSH client authentication mechanism. Possible values: PUBLICKEY PASSWORD PASSWORD_AND_PUBLICKEY PASSWORD_OR_PUBLICKEY ACCEPTED CIPHER SUITES: It lists SSL/TLS cipher suites available in the SFTP server and exposed in the DMZ Gateway. Select the cipherSuites accepted. For a list of all accepted Cipher Suites, follow this link. MAC ALGORITHMS: Possible values: HMAC_MD5 HMAC_SHA1 HMAC_MD5_96 HMAC_SHA1_96 HMAC_SHA256 HMAC_SHA2_256 HMAC_SHA2_512 KEY EXCHANGE ALGORITHMS: Possible values: DIFFIE_HELLMAN_GROUP1_SHA1 DIFFIE_HELLMAN_GROUP14_SHA1 DIFFIE_HELLMAN_GROUP14_SHA256 DIFFIE_HELLMAN_GROUP15_SHA512 DIFFIE_HELLMAN_GROUP16_SHA512 DIFFIE_HELLMAN_GROUP17_SHA512 DIFFIE_HELLMAN_GROUP18_SHA512 DIFFIE_HELLMAN_GROUP_EXCHANGE_SHA1 DIFFIE_HELLMAN_GROUP_EXCHANGE_SHA256 ECDH_SHA2_NISTP256 ECDH_SHA2_NISTP384 ECDH_SHA2_NISTP521 ACCEPTED CIPHER SUITES: It lists SSL/TLS cipher suites available in the SFTP server and exposed in the DMZ Gateway. Select the cipherSuites accepted. For a list of all accepted Cipher Suites, follow this link. |

The rsa-sha2-256 and rsa-sha2-512 signing algorithms (also called HostKeyAlgorithms) are included in the list of supported ssh-rsa and ssh-dss algorithms.
They are hard-coded, so they cannot be configured.
🚀 To change any DMZ port of an SFTP server that belongs to a peer, select the server you want to update. Next, click the pencil icon in the top-right corner of the server card. Enter the new port or ports in the appropriate fields. Finally, click the SAVE button to confirm your changes. Remember that the new port number will only affect the peer's selected server.
HTTP
| Connection | |
|---|---|
| PORT * | Enter the port to connect to the server. This is the TCP/IP port the server will listen to in the STENG node. |
| MAX SESSION | Specify the maximum number of active sessions. |
| DMZ mode | |
|---|---|
| NONE (default) | No session proxying through DMZ Gateway is applied. |
| PORT_FORWARDING | Incoming/Outgoing connections to/from the STENG server will be proxied inside an SSL tunnel without being validated in advance. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. |
| SESSION_TERMINATION | The server session will be terminated inside the DMZ Gateway before data is sent to the STENG server. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER PORT *: Enter the DMZ server port to be used for the connection. |
🚀 To change any DMZ port of an HTTP server that belongs to a peer, select the server you want to update. Next, click the pencil icon in the top-right corner of the server card. Enter the new port or ports in the appropriate fields. Finally, click the SAVE button to confirm your changes. Remember that the new port number will only affect the peer's selected server.
HTTPS
| Connection | |
|---|---|
| PORT * | Enter the port to connect to the server. This is the TCP/IP port the server will listen to in the STENG node. |
| SERVER KEYLABEL * | Enter the Key identifier of the keystore store to select the Private Key and Certificate to create an SSL connection. |
| MAX SESSION | Specify the maximum number of active sessions. |
| CONNECTION TIMEOUT | Define the number of seconds to wait without network activity before closing a session due to inactivity. Default value: 60. |
| REQUIRE CLIENT AUTHENTICATION | Enable the toggle button if you want the server to require SSL Client Authentication from the client that is connecting. If enabled, the CLIENT CERTIFICATION MATCH field appears, and the appropriate option must be selected in the drop-down menu – details are in the field below. |
| CLIENT CERTIFICATION MATCH | This field appears if the Require Client Authentication button is enabled. It defines if the Certificate required for Client Authentication will be matched and how. Possible values: - NONE: the Certificate will not be matched. The presence of a valid Certificate is enough to proceed. This is the less secure option. - CNEQUALS (default value): the Common Name field of the Certificate must be the same as the user name. This is the most restrictive option. - CNCONTAINS: the Common Name field of the Certificate must contain the user name. |
| AUTHENTICATION PROTOCOL | Select the SSL authentication protocol. Possible values: - ALL - ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1_1 TLSv1_2 TLSv1_3 SSLv2Hello |
| ACCEPTED CIPHER SUITES | Select the cipherSuites accepted to establish an SSL connection. For a list of all accepted Cipher Suites, follow this link. |
| DMZ mode | |
|---|---|
| NONE (default) | No session proxying through DMZ Gateway appli. |
| PORT_FORWARDING | Incoming/Outgoing connections to/from the STENG server will be proxied inside an SSL tunnel without being validated in advance. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. |
| SESSION_TERMINATION | The server session will be terminated inside the DMZ Gateway before data is sent to the STENG server. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER PORT *: Enter the DMZ server port to be used for the connection. SERVER KEYLABEL: Select the label of the private key to be used by the SFTP server exposed in the DMZ Gateway. REQUIRE CLIENT AUTHENTICATION: Enable to use SSL Client authentication in DMZ. The remote X.509 client certificate will be validated by the DMZ HTTP/S server before the connection is routed to the STENG server. If enabled, the DMZ CLIENT CERTIFICATION MATCH field appears, and the appropriate option must be selected in the drop-down menu – details are in the field below. If the HTTP client on DMZGateway is connecting to an HTTP Server with clientAuthentication=true on the STENG, check the client certificate coming from the client HTTP into the Untrusted Cache. Then, trust the client certificate and check the Trust Store. DMZ CLIENT CERTIFICATION MATCH: This field appears if the Require Client Authentication button is enabled. It defines if the Certificate required for Client Authentication will be matched and how. Possible values: - NONE: the Certificate will not be matched. The presence of a valid Certificate is enough to proceed. This is the less secure option. - CNEQUALS (default value): the Common Name field of the Certificate must be the same as the user name. This is the most restrictive option. - CNCONTAINS: the Common Name field of the Certificate must contain the user name. AUTHENTICATION PROTOCOL: Select the SSL authentication protocol. Possible values: - ALL - ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1_1 TLSv1_2 SSLv2Hello ACCEPTED CIPHER SUITES: It lists SSL/TLS cipher suites available in the FTP/S server and exposed in the DMZ Gateway. Select the cipherSuites accepted. For a list of all accepted Cipher Suites, follow this link. |
🚀 To change any DMZ port of an HTTPS server that belongs to a peer, select the server you want to update. Next, click the pencil icon in the top-right corner of the server card. Enter the new port or ports in the appropriate fields. Finally, click the SAVE button to confirm your changes. Remember that the new port number will only affect the peer's selected server.
PeSIT
| Connection | |
|---|---|
| PORT * | Enter the port to connect to the server. This is the TCP/IP port the server will listen to in the STENG node. |
| DIAGNOSTIC PORT1 | Enter the Diagnostic port used by the native layer. |
| DIAGNOSTIC PORT2 | Enter the Diagnostic port used by the native layer. |
| LOCAL ID | Enter the local Pesit identifier. |
| DEFAULT FILE NAME | Enter a default file name for the file received. This is a free-text field where spaces are allowed but not suggested. |
| MAXIMUM PDU SIZE | Enter the maximum PDU size buffer. Possible values: 1 <= size <= 66000. Default value: 30000. |
| MAXIMUM SDU SIZE | Enter the maximum SDU size buffer. Possible values: 1 <= size <= 66000. Default value: 30000. |
| CONNECTION TIMEOUT | Define the number of seconds to wait without network activity before closing a session due to inactivity. |
| MAX SESSION | Enter the maximum number of active sessions. Values: 0 to 256. |
| SYNC POINT BY DATA | Enter the number of synchronization points used to restart a transfer after an incident |
| ACK WINDOW | Enter the Acknowledgement window size. Values: 0 to 255. |
| DMZ mode | |
|---|---|
| NONE (default) | No session proxying through DMZ Gateway is applied. |
| PORT_FORWARDING | Incoming/Outgoing connections to/from the STENG server will be proxied inside an SSL tunnel without being validated in advance. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. |
| SESSION_TERMINATION | The server session will be terminated inside the DMZ Gateway before data is sent to the STENG server. |
🚀 To change any DMZ port of a PeSIT server that belongs to a peer, select the server you want to update. Next, click the pencil icon in the top-right corner of the server card. Enter the new port or ports in the appropriate fields. Finally, click the SAVE button to confirm your changes. Remember that the new port number will only affect the peer's selected server.
PR4
When configured on multiple STENG peers, the PR4 server provides active-passive High Availability. This implies that outbound transport jobs and inbound transport jobs using the PR4 protocol will only run in one of the peers.
The first peer activated gets priority activation of the PR4 server.
Peers activated later will remain in idle status.
In case of deactivation or crash of the first peer, the system will assign activation priority to one of the other peers that are still active.
In mini systems (i.e., excluding zOS), idle servers are activated in mirror mode in order to redirect incoming traffic to the one and only active server.
Note: Intentionally stopping the PR4 server in the peer that holds the PR4 activation priority does not change the configuration of the priority assignment. So, PR4 transport jobs will not be executed until the server is started.
| Connection | |
|---|---|
| PORT * | Enter the port to connect to the server. This is the TCP/IP port the server will listen to in the STENG node. |
| NODE NAME * | Enter the SPAZIO system local name. |
| QMANAGER NAME * | Enter the SPAZIO local Queue Manager. |
| SERVER KEYLABEL | Select the key identifier about the keystore store to select Private Key and Certificate to create an SSL connection. |
| PPS COMPRESSION SUPPORT | Enable if the server must accept compression using PPS. |
| PPS HASH ALGORITHM | Select the algorithm used by PPS for hashing. Possible values: NULLHASH MD5 SHA1 SHA_256 SHA_384 SHA_512 |
| PPS CRYPTO ALGORITHM | Select the algorithm used by PPS for cryptography. Possible values: NULLCIPHER DES_CBC DES3_CBC RC4 DES3_CBC_EDE2 AES256_CTR AES192_CTR AES128_CTR |
| DMZ mode | |
|---|---|
| NONE (default) | No session proxying through DMZ Gateway is applied. |
| PORT_FORWARDING | Incoming/Outgoing connections to/from the STENG server will be proxied inside an SSL tunnel without being validated in advance. OUTGOING LINE IPADDR *: Enter the address used by outgoing connections via DMZ. OUTGOING LINE PORT *: Enter the port used by outgoing connections via DMZ. |
| SESSION_TERMINATION | The server session will be terminated inside the DMZ Gateway before data is sent to the STENG server. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER PORT *: Enter the DMZ server port to be used for the connection. OUTGOING LINE IPADDR *: Enter the address used by outgoing connections via DMZ. OUTGOING LINE PORT *: Enter the port used by outgoing connections via DMZ. |
🚀 To change any DMZ port of a PR4 server that belongs to a peer, select the server you want to update. Next, click the pencil icon in the top-right corner of the server card. Enter the new port or ports in the appropriate fields. Finally, click the SAVE button to confirm your changes. Remember that the new port number will only affect the peer's selected server.
PR5
| Connection | |
|---|---|
| PORT * | Enter the port to connect to the server. This is the TCP/IP port the server will listen to in the STENG node. |
| QMANAGER NAME * | Enter the SPAZIO local Queue Manager. Maximum 48 characters. |
| DEFAULT CHARSET * | Select the default charset used to convert the received text in the external file. For a list of the default charsets, follow this link. |
| SERVER KEYLABEL * | Select the key identifier about the keystore store to select Private Key and Certificate to create an SSL connection. |
| AUTHENTICATION PROTOCOL | Select the SSL authentication protocol. Possible values: ALL ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1_1 TLSv1_2 TLSv1_3 SSLv2Hello |
| ACCEPTED CIPHER SUITES | Select the cipherSuites accepted to establish an SSL connection. For a list of all accepted Cipher Suites, follow this link. |
| REQUIRE CLIENT AUTHENTICATION | Enable the toggle button if SSL Client authentication must be required. |
| DMZ mode | |
|---|---|
| NONE (default) | No session proxying through DMZ Gateway is applied. |
| PORT_FORWARDING | Incoming/Outgoing connections to/from the STENG server will be proxied inside an SSL tunnel without being validated in advance. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER KEYLABEL: Select the label of the private key to be used by the SFTP server exposed in the DMZ Gateway. AUTHENTICATION PROTOCOL: Select the SSL authentication protocol. Possible values: ALL ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1_1 TLSv1_2 TLSv1_3 SSLv2Hello ACCEPTED CIPHER SUITES: For a list of all accepted Cipher Suites, follow this link. REQUIRE CLIENT AUTHENTICATION: Enable the toggle button if SSL Client authentication must be required. |
| SESSION_TERMINATION | The server session will be terminated inside the DMZ Gateway before data is sent to Sthe TENG server. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER PORT *: Enter the DMZ server port to be used for the connection. SERVER KEYLABEL: Select the label of the private key to be used by the SFTP server exposed in the DMZ Gateway. AUTHENTICATION PROTOCOL: Select the SSL authentication protocol. Possible values: ALL ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1_1 TLSv1_2 TLSv1_3 SSLv2Hello ACCEPTED CIPHER SUITES: For a list of all accepted Cipher Suites, follow this link. REQUIRE CLIENT AUTHENTICATION: Enable the toggle button if SSL Client authentication must be required. |
🚀 To change any DMZ port of a PR5 server that belongs to a peer, select the server you want to update. Next, click the pencil icon in the top-right corner of the server card. Enter the new port or ports in the appropriate fields. Finally, click the SAVE button to confirm your changes. Remember that the new port number will only affect the peer's selected server.
PR5S
| Connection | |
|---|---|
| PORT * | Enter the port to connect to the server. This is the TCP/IP port the server will listen to in the STENG node. |
| QMANAGER NAME * | Enter the SPAZIO local Queue Manager. Maximum 48 characters. |
| DEFAULT CHARSET * | Select the default charset used to convert the received text in the external file. For a list of the default charsets, follow this link. |
| SERVER KEYLABEL * | Select the key identifier of the keystore store to select Private Key and Certificate to create an SSL connection. |
| AUTHENTICATION PROTOCOL | Select the SSL authentication protocol. Possible values: ALL ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1_1 TLSv1_2 TLSv1_3 SSLv2Hello |
| ACCEPTED CIPHER SUITES | Select the cipherSuites accepted to establish an SSL connection. For a list of all accepted Cipher Suites, follow this link. |
| 🚀REQUIRE CLIENT AUTHENTICATION | Enable the toggle button if you want the server to require SSL Client Authentication from the client that is connecting. If enabled, the CLIENT CERTIFICATION MATCH field appears, and the appropriate option must be selected in the drop-down menu – details are in the field below. |
| 🚀 CLIENT CERTIFICATION MATCH | This field appears if the Require Client Authentication button is enabled. It defines if the Certificate required for Client Authentication will be matched and how. Possible values: - NONE: the Certificate will not be matched. The presence of a valid Certificate is enough to proceed. This is the less secure option. - CNEQUALS (default value): the Common Name field of the subject of the Certificate must be exactly the same as the user name. This is the most restrictive option. - CNCONTAINS: the Common Name field of the subject of the Certificate must contain the user name. |
| DMZ mode | |
|---|---|
| NONE (default) | No session proxying through DMZ Gateway is applied. |
| PORT_FORWARDING | Incoming/Outgoing connections to/from the STENG server will be proxied inside an SSL tunnel without being validated in advance. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER KEYLABEL: Select the label of the private key to be used by the SFTP server exposed in the DMZ Gateway. AUTHENTICATION PROTOCOL: Select the SSL authentication protocol. Possible values: ALL ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1_1 TLSv1_2 TLSv1_3 SSLv2Hello ACCEPTED CIPHER SUITES: For a list of all accepted Cipher Suites, follow this link. REQUIRE CLIENT AUTHENTICATION: Enable the toggle button if SSL Client authentication must be required. |
| SESSION_TERMINATION | The server session will be terminated inside the DMZ Gateway before data is sent to the STENG server. DMZ PROXY PORT *: This port represents the tunnel that is opened for connection with the STENG Server. SERVER PORT *: Enter the DMZ server port to be used for the connection. SERVER KEYLABEL: Select the label of the private key to be used by the SFTP server exposed in the DMZ Gateway. AUTHENTICATION PROTOCOL: Select the SSL authentication protocol. Possible values: ALL ONLY SPECIFIC VALUES: SSLv3 TLSv1 TLSv1_1 TLSv1_2 TLSv1_3 SSLv2Hello ACCEPTED CIPHER SUITES: For a list of all accepted Cipher Suites, follow this link. REQUIRE CLIENT AUTHENTICATION: Enable the toggle button if SSL Client authentication must be required. |
🚀 To change any DMZ port of a PR5S server that belongs to a peer, select the server you want to update. Next, click the pencil icon in the top-right corner of the server card. Enter the new port or ports in the appropriate fields. Finally, click the SAVE button to confirm your changes. Remember that the new port number will only affect the peer's selected server.
CD
| Connection | |
|---|---|
| EVENT POLLING BATCH SIZE | Enter the maximum quantity of Connect:Direct statistics read at each poll; this is necessary to verify that a file is ready to be got. |
| PORT * | Enter the API command port of the Connect:Direct server. |
| HOST * | Enter the IP Address of the Connect:Direct server. |
| NODE NAME * | Enter the name of the Connect:Direct node. |
| USER * | Enter the Username to connect to the Connect:Direct node. |
| PASSWORD * | Enter the password to connect to the Connect:Direct node. |
| SHARED FOLDER WITH C:D SERVER * | Enter the folder shared with the server. |
| CONNECTION TIMEOUT | Enter the number of seconds without network activity to wait before closing a session due to inactivity. Default value: 60. |
| DMZ cannot be used with this protocol |
|---|
| Note: The first time the C:D server is started, the "trnx/cd" folder is created in the directory shared among the STENGs of the Cluster. Information about the files exchanged between Data One and the C:D Server is written in this folder. Moreover, it is used to manage the C:D Server statistics. |
Updated 24 days ago
