Data One common domain topology patterns
In the next few sections, we discuss Data One topology patterns, i.e. typical ways of deploying Data One platform modules across all domain nodes.
While the reported scenarios are recurring and typical, by no means do they cover all the allowed combinations. So, your actual production topology may differ from the reported ones, due to environment-specific functional / non-functional requirements or constraints.
Note: DOIM and control node are not depicted for simplicity reasons, but clearly a node playing the role of control node and hosting DOIM must always be present and capable of connecting to all other nodes in the domain, as explained at the beginning of this chapter.
1-tier (single node) - Data Mover (with DMZ), Data Watcher and Data Shaper

In this topology pattern, a single machine runs one instance of all these components:
CEMAN
Data Watcher
STENG
Data Shaper
DMZ
This topology pattern is mainly meant for experimentation and testing purposes, as it lacks the scalability and availability typically required in production environments.
On top of that, running DMZ on the same machine as STENG, although technically feasible, voids DMZ of its proxying architectural role, which makes it useless.
2-tiers - Data Mover, Data Watcher and Data Shaper

In this topology pattern, components are distributed across two tiers of machines, each of which is independently clustered and scaled, more precisely:
Tier 1 - Command & Control and Monitoring Tier, made of 3 machines, each of which runs on instance of these components:
CEMAN
Data Watcher
Tier 2 - Executive Tier, made of 2 machines, each of which runs one instance of these components:
STENG
Data Shaper
This pattern is typically adopted for MFT-oriented scenarios.
3-tiers - Data Mover (with DMZ), Data Watcher and Data Shaper

In this topology pattern, components are distributed across three tiers of machines, each of which is independently clustered and scaled, more precisely:
Tier 1 - Command & Control and Monitoring Tier, made of 3 machines, each of which runs one instance of these components:
CEMAN
Data Watcher
Tier 2 - Executive Tier, made of 2 machines, each of which runs one instance of these components:
STENG
Data Shaper
Tier 3 - Proxying Tier, made of 2 machines, each of which runs one instance of this component:
DMZ
4-tiers - Data Mover (with DMZ), Data Watcher and Data Shaper
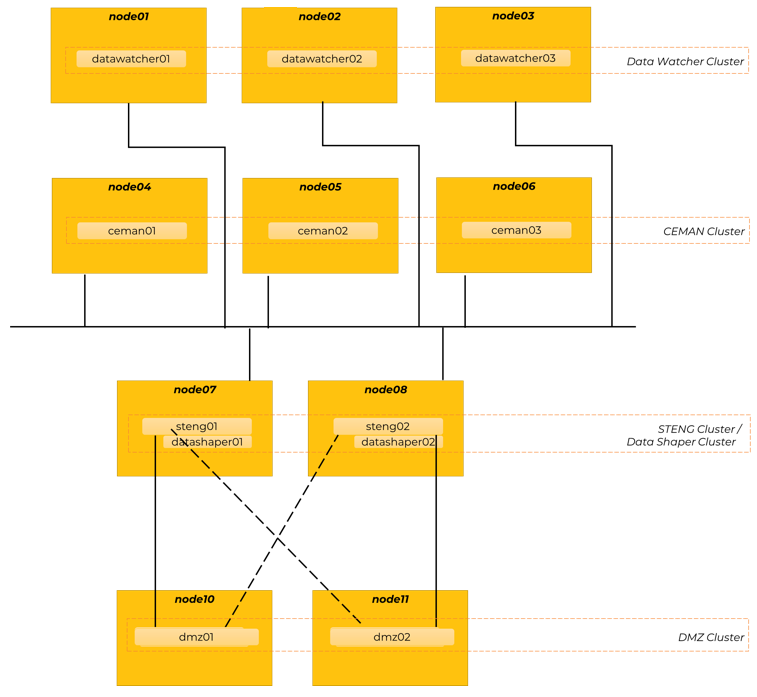
In this topology pattern, components are distributed across four tiers of machines, each of which is independently clustered and scaled, more precisely:
Tier 1 – Monitoring Tier, made of 3 machines, each of which runs one instance of this component:
Data Watcher
Tier 2 - Command & Control Tier, made of 3 machines, each of which runs one instance of this component:
CEMAN
Tier 3 - Executive Tier, made of 2 machines, each of which runs one instance of these components:
STENG
Data Shaper
Tier 4 - Proxying Tier, made of 2 machines, each of which runs one instance of this component:
DMZ
Last updated